Search for "Isa" returned 9794 results

33 min
Ceph Manager Dashboard
How do I manage such a big cluster?
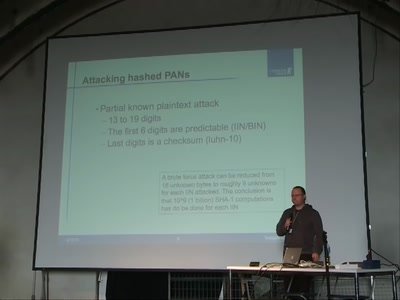
51 min
Strong encryption of credit card information
Attacks on common failures when encrypting credit card…

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows
46 min
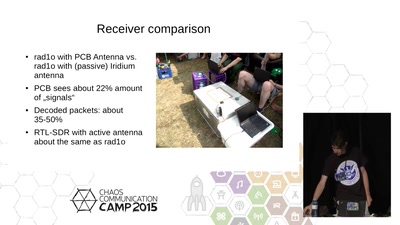
Iridium Hacking
please don't sue us
50 min
Vintage programming: an archaeological journey into the past
How software development evolved in the last 30 years
66 min
Hacking DNA
Compiling code for living systems

38 min
What your phone won’t tell you
Uncovering fake base stations on iOS devices

40 min
A year of surveillance in France: a short satirical tale by La Quadrature du Net
From the so-called Country of human rights to a…
58 min
Are all BSDs created equally?
A survey of BSD kernel vulnerabilities.

41 min
Chaos Communication Chemistry
DNA security systems based on molecular randomness
40 min
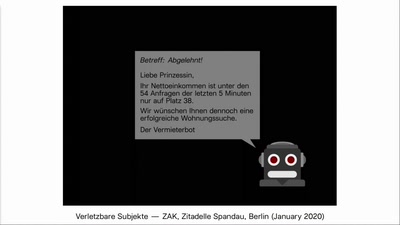
Wohnungsbot: An Automation-Drama in Three Acts
A media-art project which automates the search for flats in…
28 min
Adding Salt to AutoYaST
Integration between AutoYaST and Configuration Management…
44 min