Search for "Nico" returned 1170 results

42 min
Jugend Hackt
Chaos Family
60 min
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP

62 min
radare demystified
after 1.0

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches
38 min
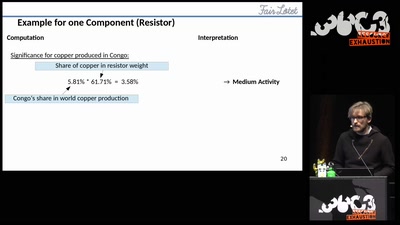
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices

63 min
Through a PRISM, Darkly
Everything we know about NSA spying
39 min
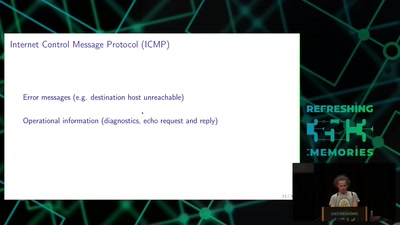
Transmission Control Protocol
TCP/IP basics

69 min
Telescope Making
How to make your own telescope
56 min
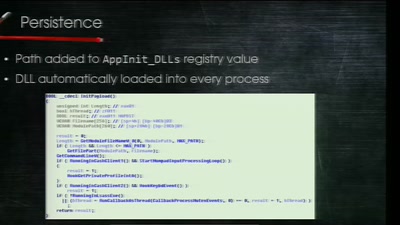
Electronic Bank Robberies
Stealing Money from ATMs with Malware

55 min
What is Good Technology?
Answers & practical guidelines for engineers.
63 min
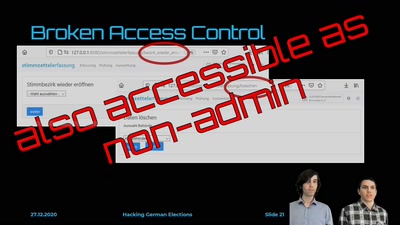
Hacking German Elections
Insecure Electronic Vote Counting - How It Returned and Why…
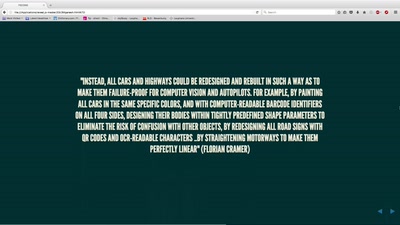
35 min
Ethics in the data society
Power and politics in the development of the driverless car

45 min
![Why we are addicted to lithium [2/2]](https://static.media.ccc.de/media/events/rc3/2021/194-17816a45-eea7-5b85-b623-5f343aec59de.jpg)