Search for "Jella" returned 82 results

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

40 min
Psychedelic Medicine - Hacking Psychiatry?!
Psychedelic Therapy as a fundamentally new approach to…
60 min
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…
61 min
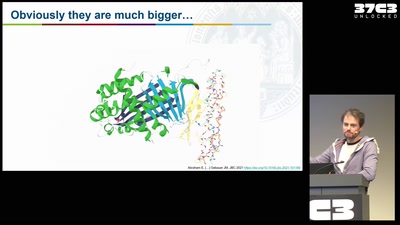
AlphaFold – how machine learning changed structural biology forever (or not?)
Getting first-hand insights into the impact of machine…

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

60 min
Mein Bot, der Kombattant
Operative Kommunikation im digitalen Informationskrieg
113 min