Search for "JO" returned 10054 results

46 min
OWASP TOP 10
Edition 2017 - Latest & Greatest

26 min
Don't scan, just ask
A new approach of identifying vulnerable web applications
65 min
Cryptographic key recovery from Linux memory dumps
Does dm-crypt and cryptoloop provide expected security when…
44 min
Unusual Web Bugs
A Web Hacker's Bag O' Tricks

38 min
Quantum Entanglement
An introduction
55 min
3D printing on the moon
The future of space exploration
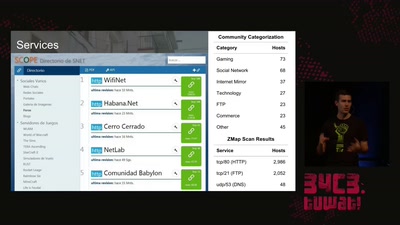
58 min
The Internet in Cuba: A Story of Community Resilience
Get a unique tour of some of the world’s most unusual…

64 min
Tor is Peace, Software Freedom is Slavery, Wikipedia is Truth
The political philosophy of the Internet

45 min
Finding and Preventing Buffer Overflows
An overview of static and dynamic approaches

62 min