Search for "Ron" returned 9415 results
44 min
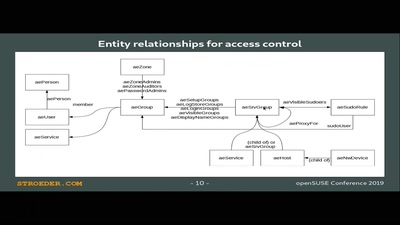
Æ-DIR -- Authorized Entitites Directory
Identity and Access Management with OpenLDAP
45 min
Open Source Firmware
... and I finally had my personal bootsplash screen :)

44 min
Garden Space Program
Mars-Missionen im eigenen Garten
59 min
International Cyber Jurisdiction
Kill Switching” Cyberspace, Cyber Criminal Prosecution &…

58 min
Collapsing the European security architecture
More security-critical behaviour in Europe!
51 min
SCADA and PLC Vulnerabilities in Correctional Facilities
Tiffany Rad, Teague Newman, John Strauchs
24 min
From Physical to Cloud to Container
One system to deploy and manage them all

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

26 min
Data Mining for Good
Using random sampling, entity resolution, communications…
31 min
Nerds in the news
Spending a year coding in a newsroom

64 min
Tor is Peace, Software Freedom is Slavery, Wikipedia is Truth
The political philosophy of the Internet
49 min
A short political history of acoustics
For whom, and to do what, the science of sound was…

30 min
The Magical Secrecy Tour
A Bus Trip into the Surveillance Culture of Berlin One Year…
47 min
Hillbilly Tracking of Low Earth Orbit
Repurposing an Inmarsat Dish

42 min