Search for "rem0te" returned 826 results

55 min
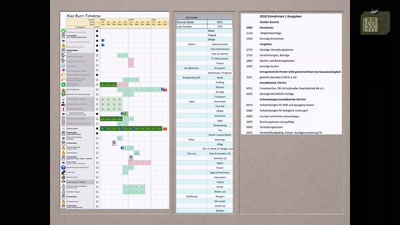
White-Box Cryptography
Survey

58 min
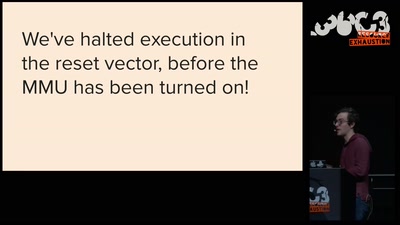
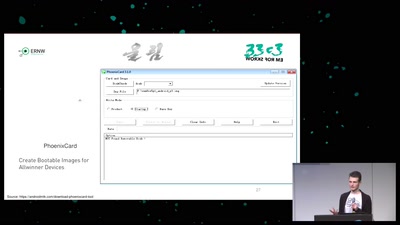
Baseband Exploitation in 2013
Hexagon challenges

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

63 min
goto fail;
exploring two decades of transport layer insecurity

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…
55 min
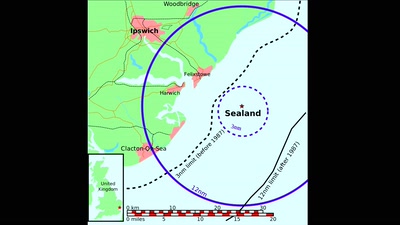
Cyber Necromancy
Reverse Engineering Dead Protocols

74 min
Die EU im Krisenmodus
Was bedeutet das für die Zukunft

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…

90 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.…

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…

62 min