Search for "Jong-Hoon Lee" returned 553 results

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

45 min
To Protect And Infect
The militarization of the Internet

60 min
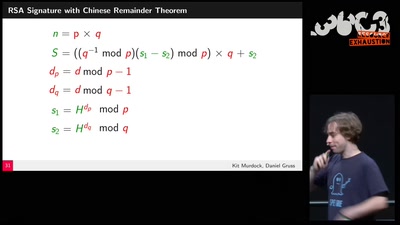
Quantum Cryptography
from key distribution to position-based cryptography

55 min
How to Build a Mind
Artificial Intelligence Reloaded

33 min
UPSat - the first open source satellite
Going to space the libre way

54 min
Tactical Embodiment
Activism and Performance In Hostile Spaces Online
49 min
SD-WAN a New Hop
How to hack software defined network and keep your sanity?
42 min
Wifibroadcast
How to convert standard wifi dongles into digital broadcast…

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

58 min
Protecting Your Privacy at the Border
Traveling with Digital Devices in the Golden Age of…
60 min
Opening Closed Systems with GlitchKit
'Liberating' Firmware from Closed Devices with Open Source…
31 min
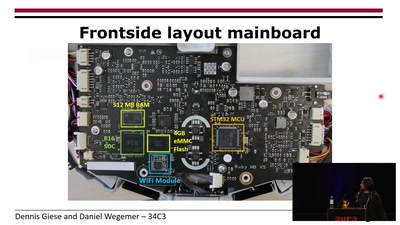
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

64 min
Cory Doctorow – Fireside Chat
Reading and Q&A

32 min