Search for "Seth Hardy" returned 899 results

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy

39 min
Tales of old: untethering iOS 11
Spoiler: Apple is bad at patching

60 min
What does Big Brother see, while he is watching?
Uncovering images from the secret Stasi archives.

61 min
About Gamma-Ray Bursts And Boats
What We (Don't) Know About the Most Energetic Events in the…

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…

43 min
Tractors, Rockets and the Internet in Belarus
How belarusian authoritarian regime is using technologies…
62 min
The Ghost in the Machine
An Artificial Intelligence Perspective on the Soul

51 min
The GNU Name System
A Decentralized PKI For Social Movements

32 min
What's It Doing Now?
The Role of Automation Dependency in Aviation Accidents

59 min
Say hi to your new boss: How algorithms might soon control our lives.
Discrimination and ethics in the data-driven society
29 min
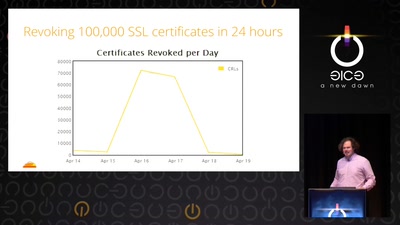
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…

32 min