Search for "sudden6" returned 98 results

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

55 min
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks

60 min
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…
91 min
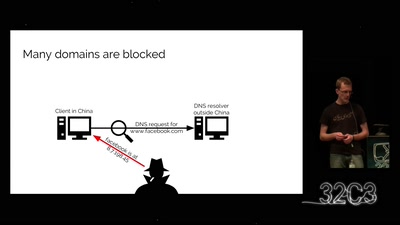
What the World can learn from Hongkong
From Unanimity to Anonymity

56 min
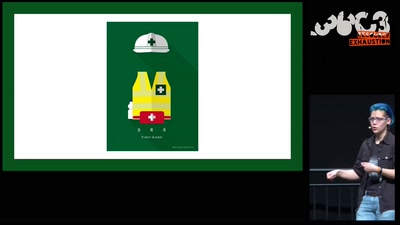
Planes and Ships and Saving Lives
How soft and hardware can play a key role in saving lives…

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…
60 min
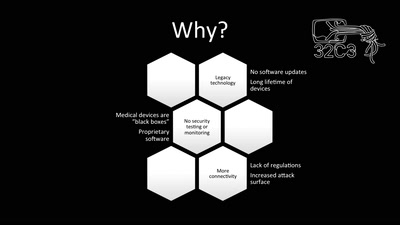
Unpatchable
Living with a vulnerable implanted device

62 min
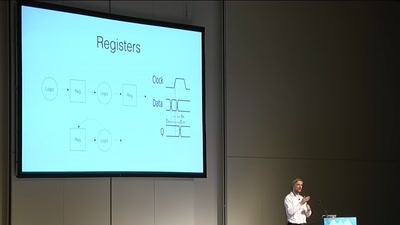
SymbiFlow - Finally the GCC of FPGAs!
A fully FOSS, Verilog to bitstream, timing driven, cross…
56 min
Deconstructing a Socialist Lawnmower
Obsolete Technologies + Critical Material Studies in Media…

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

61 min
Copywrongs 2.0
We must prevent EU copyright reform from breaking the…

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session
62 min
Public Library/Memory of the World
Access to knowledge for every member of society
56 min
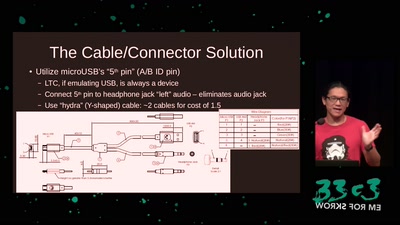
Making Technology Inclusive Through Papercraft and Sound
Introducing the Love to Code Platform

62 min
Kyber and Post-Quantum Crypto
How does it work?

61 min
The architecture of a street level panopticon
How drones, IMSI Catchers, and cameras are shaping our…
61 min
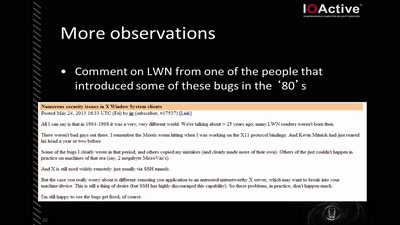
X Security
It's worse than it looks

64 min