Search for "Udo Vetter" returned 1176 results

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

60 min
Beyond your cable modem
How not to do DOCSIS networks

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…
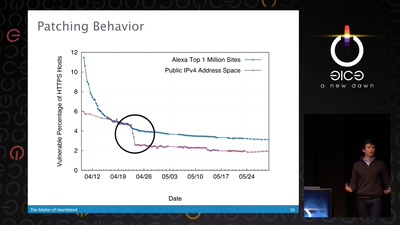
50 min
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…
42 min
Hacking the Nintendo Game & Watch
Your princess is AES encrypted in another castle

38 min
Zapfenstreich
Über Algorithmen im Krieg, aber was hat die Kunst damit…

41 min
MicroPython – Python for Microcontrollers
How high-level scripting languages make your hardware…
64 min
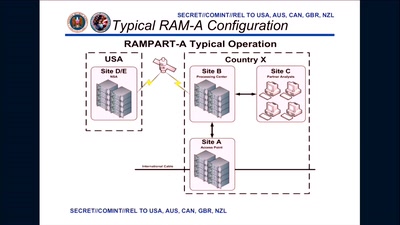
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…

60 min
Dieselgate – A year later
env stinks || exit

58 min
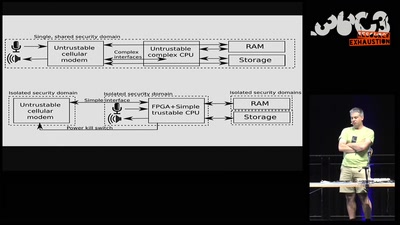
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…
49 min