Search for "Udo Vetter" returned 1176 results

42 min
A world without blockchain
How (inter)national money transfers works

60 min
Dieselgate – A year later
env stinks || exit

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…
61 min
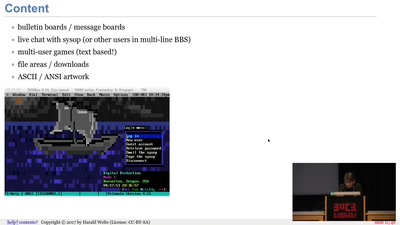
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time
40 min
Never Forgetti
a didactic live-gaming performance about dying women across…

62 min
HUMUS sapiens
Open Soil Research
61 min
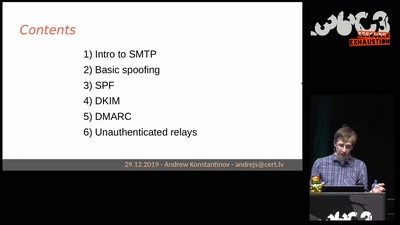
Email authentication for penetration testers
When SPF is not enough
56 min
Deconstructing a Socialist Lawnmower
Obsolete Technologies + Critical Material Studies in Media…
36 min