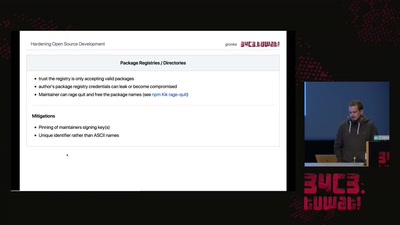
Search for "bx" returned 7029 results

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

64 min
Tor is Peace, Software Freedom is Slavery, Wikipedia is Truth
The political philosophy of the Internet
58 min