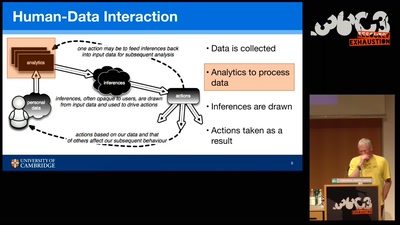
Search for "Sec" returned 2693 results
62 min
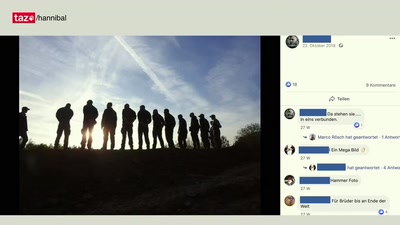
Die Affäre Hannibal
Eine erste Bilanz
56 min
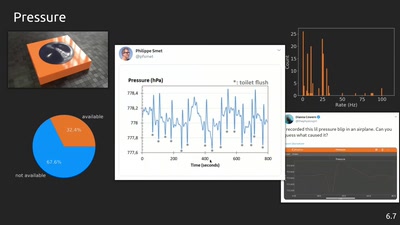
phyphox: Using smartphone sensors for physics experiments
An open source project for education, research and tinkering

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

32 min
Fuck Dutch mass-surveillance: let's have a referendum!
Forcing the Netherlands to publicly debate privacy and the…
59 min
Develop Secure Software - The DevGuard Project
OSS Security von Entwicklern für Entwickler
50 min
IRMA's Idemix core:
Understanding the crypto behind selective, unlinkable…

46 min
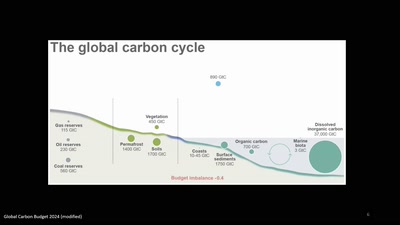
Climate Modelling
The Science Behind Climate Reports

60 min