Search for "Ben" returned 8963 results

62 min
Post Memory Corruption Memory Analysis
Automating exploitation of invalid memory writes

60 min
On working memory and mental imagery
How does the brain learn to think?

44 min
The Realtime thing
What the heck is realtime - and what to do with it

46 min
Automated Exploit Detection in Binaries
Finding exploitable vulnerabilities in binaries

63 min
Transparency and Privacy
The 7 Laws of Identity and the Identity Metasystem

45 min
ESXi Beast
Exploiting VMWARE ESXi Binary Protocols Using CANAPE
36 min
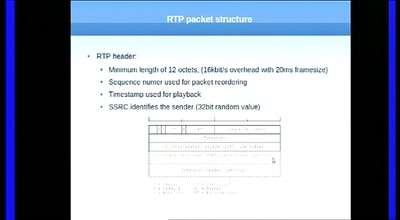
Having fun with RTP
„Who is speaking???“

50 min
Fnord News Show (English interpretation)
We help in seeing teh Fnords

41 min
DC+, The Protocol
Technical defense against data retention law
58 min
Linguistic Hacking
How to know what a text in an unknown language is about?

43 min
Nintendo DS
Introduction and hacking
58 min
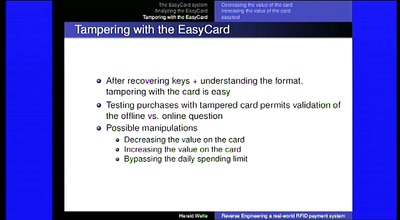
Reverse Engineering a real-world RFID payment system
Corporations enabling citizens to print digital money

50 min
Predictable RNG in the vulnerable Debian OpenSSL package
the What and the How
86 min
Certified programming with dependent types
Because the future of defense is liberal application of math

65 min
Blinkenlights Stereoscope
Behind the scenes of the new light installation

52 min
The engineering part of social engineering
Why just lying your way in won't get you anywhere

52 min
Stuff you don't see - every day
GNU Radio Internals - how to use the Framework

61 min
The A5 Cracking Project
Practical attacks on GSM using GNU Radio and FPGAs

57 min
C64-DTV Hacking
Revisiting the legendary computer in a joystick

52 min
Recent Developments in EU Data Retention proposals
Commission vs. Council - the lesser of two evils?

57 min
Hacking SCADA
how to own critical infrastructures

48 min