Search for "sec" returned 2715 results

40 min
Domain computers have accounts, too!
Owning machines through relaying and delegation
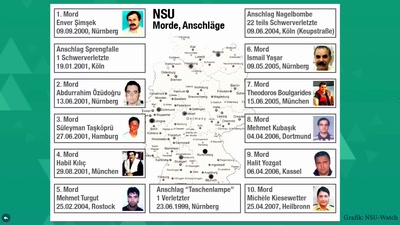
63 min
"Das ist mir nicht erinnerlich." − Der NSU-Komplex heute
Fünf Monate nach dem Urteil im ersten NSU-Prozess
31 min
Growing Up Software Development
From Hacker Culture to the Software of the Future

60 min
Are machines feminine?
exploring the relations between design and perception of…
63 min
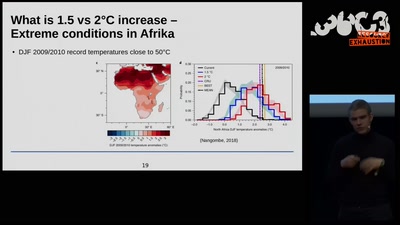
Science for future?
What we can and need to change to keep climate change low -…
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…

42 min
Make your tests fail
How randomisation adds a whole new dimension to finding…

63 min