Search for "Lea" returned 1911 results
58 min
Hacking how we see
A way to fix lazy eye?

52 min
SiliVaccine: North Korea's Weapon of Mass Detection
How I Learned to Stop Worrying and Love the Backdoor
47 min
Tightening the Net in Iran
The Situation of Censorship and Surveillance in Iran, and…
37 min
Code BROWN in the Air
A systemic update of sensitive information that you sniff…

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…
26 min
Against Metadata
Twisting time and space to explore the unknown

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting
61 min
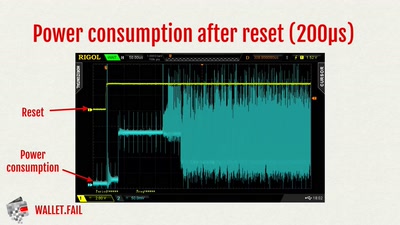
wallet.fail
Hacking the most popular cryptocurrency hardware wallets

51 min
How to drift with any car
(without your mom yelling at you)

30 min
On Computing Numbers, with an Application to Problems of our Society
Journalism ♥ Computer Science

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

38 min
What your phone won’t tell you
Uncovering fake base stations on iOS devices

47 min
The KGB Hack: 30 Years Later
Looking back at the perhaps most dramatic instance of…

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
59 min
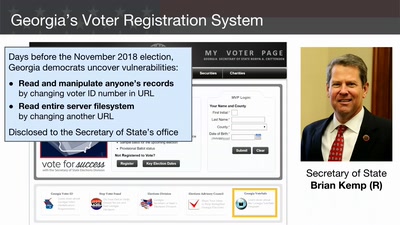
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?

49 min