Search for "Sec" returned 2697 results
61 min
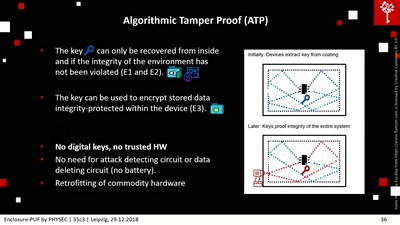
Enclosure-PUF
Tamper Proofing Commodity Hardware and other Applications

124 min
Die Open-Source-Software
Vorstellung ausgewählter Projekte
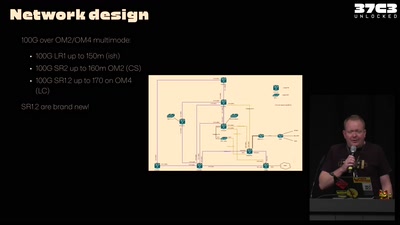
71 min
37C3 Infrastructure Review
Teams presenting how they helped making this awesome event
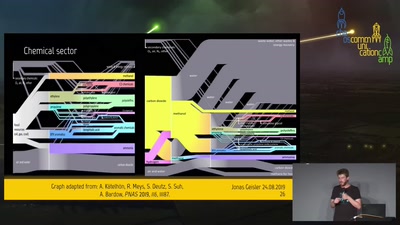
47 min
Power-to-X
How to make (nearly) everything from electricity.

50 min
How does the Internet work?
An explanation of Inter-Net and everyday protocols

41 min
Breathing Life into Legacy: An Open-Source Emulator of Legacy Apple Devices
A Dive into Reverse Engineering and Understanding the iPod…

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…
41 min
Demoscene now and then
The demoscene is an underground computer art culture.

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database
60 min
Ghidra - An Open Source Reverse Engineering Tool
How the NSA open-sourced all software in 2019

32 min