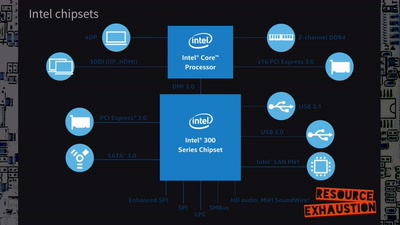
Search for "Tim Sutton" returned 302 results

33 min
Turing Complete User
What can be done to protect the term, the notion and the…
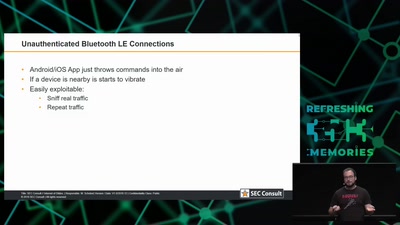
32 min
Internet of Dongs
A long way to a vibrant future
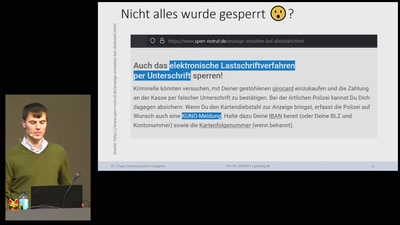
54 min
Oh no: KUNO - Gesperrte Girocards entsperren
Über „Girodays“ & anderen Kuriositäten

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

29 min
The Urban Organism
Hacking [in] Hong Kong

60 min
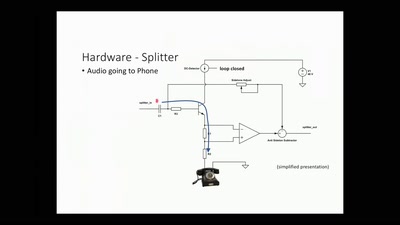
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits

32 min
The Case for Scale in Cyber Security
Security Track Keynote

52 min
SiliVaccine: North Korea's Weapon of Mass Detection
How I Learned to Stop Worrying and Love the Backdoor

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

60 min
What does Big Brother see, while he is watching?
Uncovering images from the secret Stasi archives.
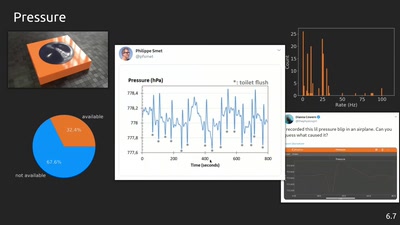
56 min
phyphox: Using smartphone sensors for physics experiments
An open source project for education, research and tinkering
60 min