Search for "Sec" returned 2697 results

32 min
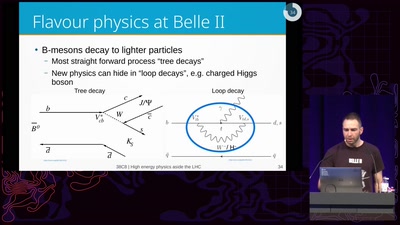
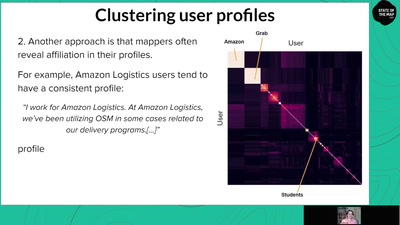
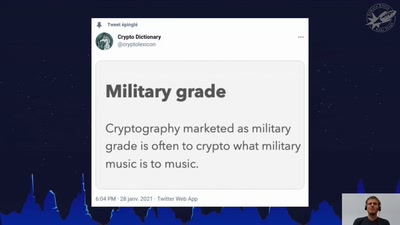
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
41 min
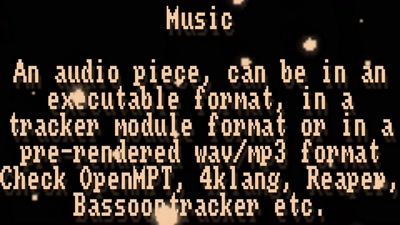
Demoscene now and then
The demoscene is an underground computer art culture.

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

37 min
Digitale Rohstoffe erhalten sich anders
Über Ampeln und den Erhalt eines Rohstoffes namens Software

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation

61 min
Vacuum robot security and privacy
prevent your robot from sucking your data

31 min
Extended DNA Analysis
Political pressure for DNA-based facial composites
59 min
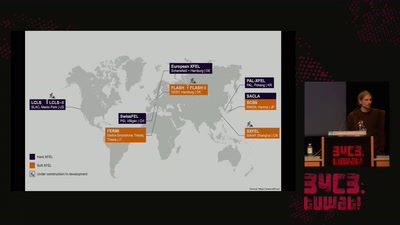
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.

44 min
Lützerath Lebt! Einblicke in den Widerstand
Für globale Klimagerechtigkeit kämpfen
58 min
Firebird Open Source Database Quick Start
Why Firebird is a powerful alternative database system
53 min
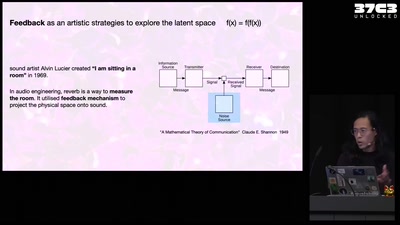
Self-cannibalizing AI
Artistic Strategies to expose generative text-to-image…

40 min
Fuzz Everything, Everywhere, All at Once
Advanced QEMU-based fuzzing

40 min
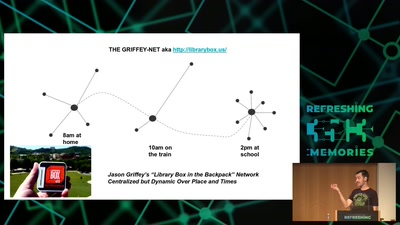
What is this? A machine learning model for ants?
How to shrink deep learning models, and why you would want…
60 min