Search for "Dave" returned 3288 results

55 min
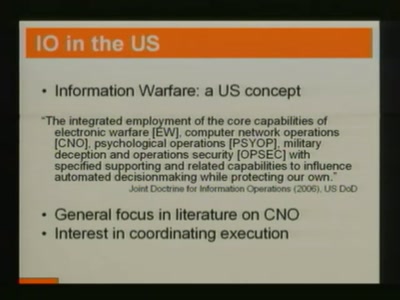
Our daily job: hacking the law
The key elements of policy hacking
53 min
Crouching Powerpoint, Hidden Trojan
An analysis of targeted attacks from 2005 to 2007
60 min
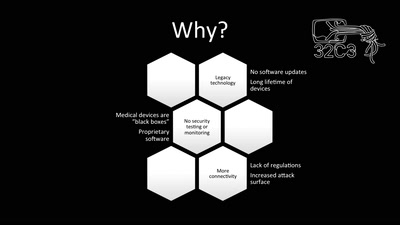
Unpatchable
Living with a vulnerable implanted device

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

57 min
Cryptowars 2.0: Lessons from the past, for the present
It's not only Hollywood who is out of ideas
51 min
SCADA and PLC Vulnerabilities in Correctional Facilities
Tiffany Rad, Teague Newman, John Strauchs

38 min
Autodafé: An Act of Software Torture
Presentation of an innovative buffer overflow uncovering…

61 min
The architecture of a street level panopticon
How drones, IMSI Catchers, and cameras are shaping our…
48 min
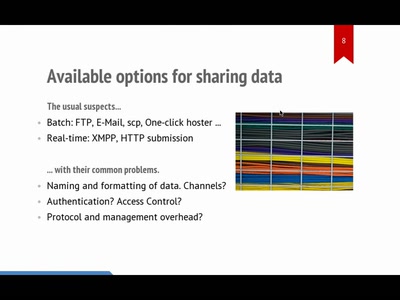
hpfriends: real-time social data-sharing
publish-subscribe feeds + trust relationship network
60 min
So you want to build a satellite?
How hard can it be? An introduction into CubeSat development

18 min