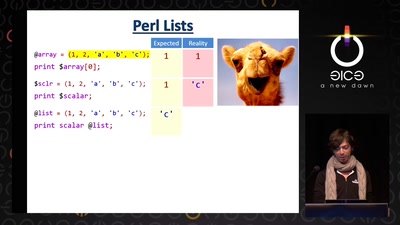
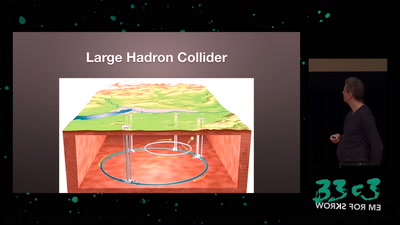
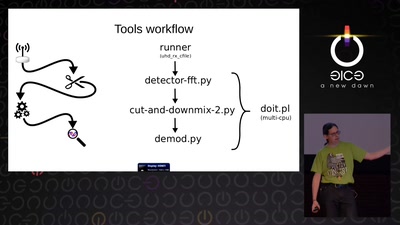
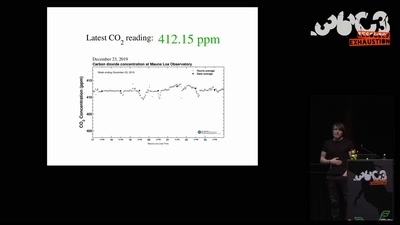
Search for "Sven" returned 2151 results

62 min
Tell no-one
A century of secret deals between the NSA and the telecom…

60 min
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…

51 min
The GNU Name System
A Decentralized PKI For Social Movements

50 min
Internet censorship in the Catalan referendum
Overview of how the state censored and how it got…
47 min
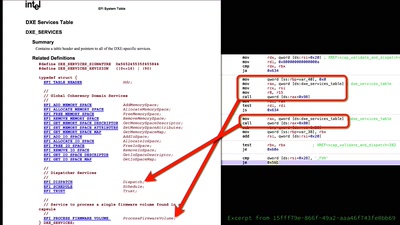
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide

64 min
Magic Lantern
Free Software on Your Camera

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

59 min
Security of the IC Backside
The future of IC analysis

63 min
Dissecting HDMI
Developing open, FPGA-based capture hardware for conference…

60 min
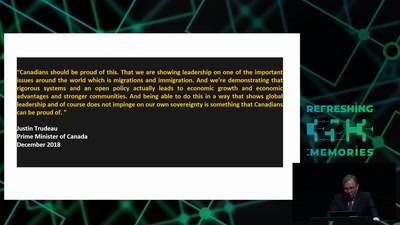
net neutrality: days of future past?
Taking stock after two years of net neutrality in the…
59 min
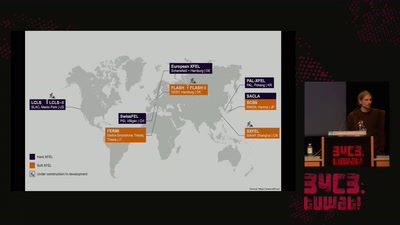
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.
31 min
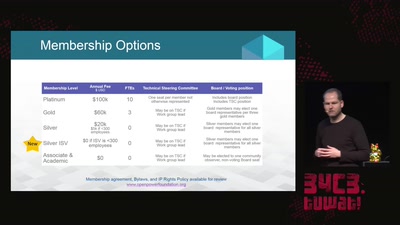
openPower - the current state of commercial openness in CPU development
is there no such thing as open hardware?
59 min