Search for "feh" returned 1848 results
37 min
Information Biology - Investigating the information flow in living systems
From cells to dynamic models of biochemical pathways and …
63 min
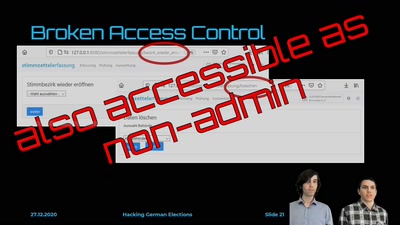
Hacking German Elections
Insecure Electronic Vote Counting - How It Returned and Why…

62 min
SymbiFlow - Finally the GCC of FPGAs!
A fully FOSS, Verilog to bitstream, timing driven, cross…
44 min
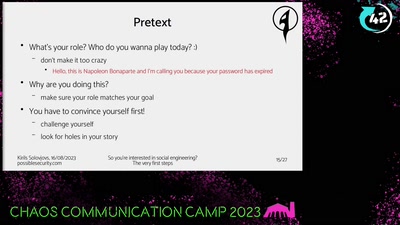
So you're interested in social engineering?
The very first steps

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
109 min
Fnord-Jahresrückblick-Rückblick
20 Jahre Fnord-Jahresrückblick!
40 min
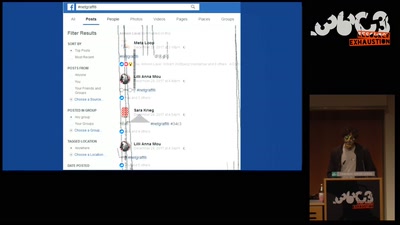
Art against Facebook
Graffiti in the ruins of the feed and the…

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques

43 min
#NoPNR – Let’s kill the next Data Retention Law
How to Stop the Dubious Use of Passenger Name Records by…

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI
38 min
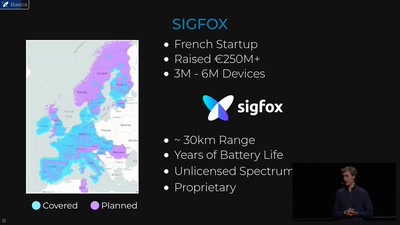
Hunting the Sigfox: Wireless IoT Network Security
Dissecting the radio protocol of Sigfox, the global…
29 min
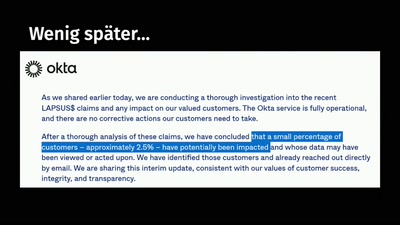
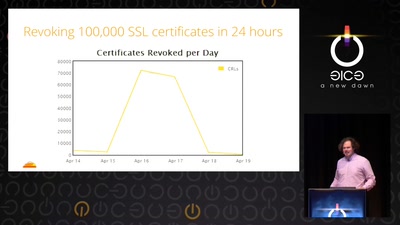
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…

63 min
Reconstructing narratives
transparency in the service of justice

85 min
Erklär ma:
Solarenergie

60 min