Search for "Ben" returned 8978 results
53 min
Solid rocket engines
Design and implementation of engines with solid propellant

60 min
An Introduction to Traffic Analysis
Attacks, Defences and Public Policy Issues...

55 min
The Web according to W3C
How to turn your idea into a standard

56 min
Sport für Nerds
discover your body

97 min
Tap the Electronic Frontier Foundation
EFF staffers answer your questions!
37 min
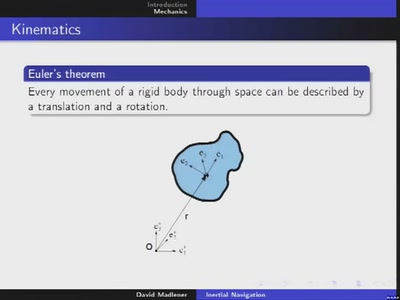
Inertial navigation
Rigid body dynamics and its application to dead reckoning
146 min
Lightning Talks 2
5 Minutes of Fame

39 min
DIY Survival
How to survive the apocalypse or a robot uprising

46 min
The Ethics of Activist DDOS Actions
A Historical Analysis

58 min
Counterlobbying EU institutions
How to attempt to counter the influence of industry…
60 min
Open Source Lobbying, tips from the trenches
From one angry e-mail to writing national policy on open…

68 min
Software Protection and the TPM
The Mac OS X Story

51 min
Culture Jamming & Discordianism
Illegal Art & Religious Bricolage

40 min
Data Mining Your City
Early lessons in open city data from Philadelphia, PA, USA

56 min
Corp vs. Corp
Profiling Modern Espionage

64 min
What is in a name?
Identity-Regimes from 1500 to the 2000s

60 min
Black Ops Of TCP/IP 2005.5
New Explorations: Large Graphs, Larger Threats
107 min
Pentanews Game Show 2k11/3
42 new questions, new jokers, same concept, more fun than…
57 min