Search for "Ray" returned 3325 results

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

51 min
Reverse Engineering the MOS 6502 CPU
3510 transistors in 60 minutes
20 min
Ceph, ELK & opensuse
This talk will be held by Denys Kondratenko and Abhishek…
36 min
Visualization of networks using physics
How algorithms inspired by the laws of physics can create…
60 min
Ghidra - An Open Source Reverse Engineering Tool
How the NSA open-sourced all software in 2019

66 min
BOLSONARO IS AN ENVIRONMENTAL CATASTROPH!
How the rise of bolsonsarism culminate in the Burning of…

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it
58 min
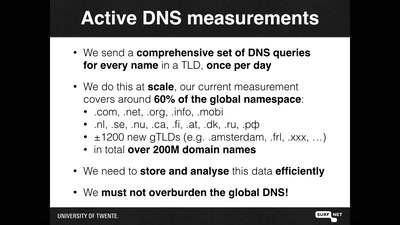
OpenINTEL: digging in the DNS with an industrial size digger
I measured 60% of the DNS, and I found this

55 min