Search for "ths" returned 8305 results

66 min
Free and Open Source Software in the Developing World
(and aren't we all developing?)

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
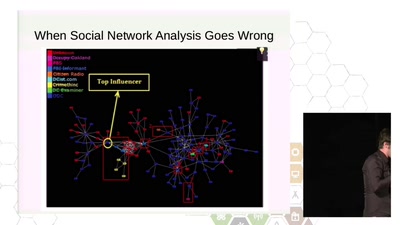
60 min
Resisting Surveillance: it's is not just about the metadata
The infiltration and physical surveillance of social…
43 min