Search for "Jon" returned 9532 results
65 min
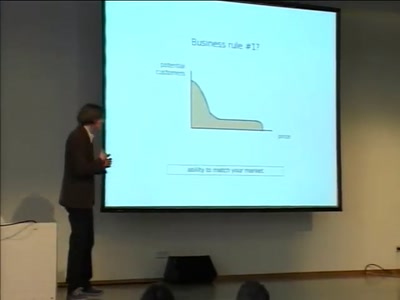
Overtaking Proprietary Software Without Writing Code
"a few rough insights on sharpening free software"
60 min
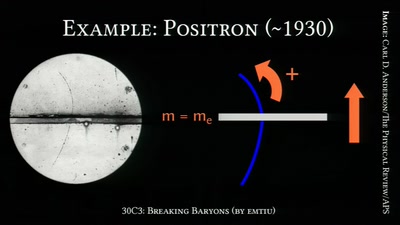
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders
30 min
kubernetes for toasters?
potential solutions to achieving containerization on…

57 min
Why Net Neutrality Matters?
Status update on current legislation, campaigns and actions

48 min
Moonbounce Radio Communication
To the Moon and back in two seconds. The joy of light speed…

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

39 min
Analog Computing
High performance/low power computing based on the analog…
138 min
Enemies of the State: What Happens When Telling the Truth about Secret US Government…
Blowing the Whistle on Spying, Lying & Illegalities in the…

52 min
Freedom of expression in new Arab landscape
Spreading of new Arab satellite TV stations: consequences…
28 min
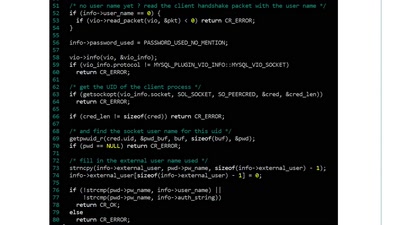
Learn how to add functionality to the MySQL server: a guided tour
Hack on the MySQL code for fun and profit !
41 min
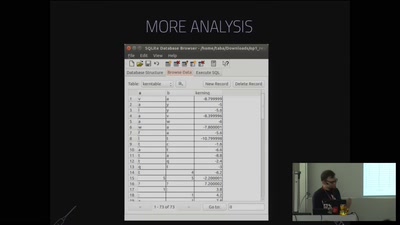
Reverse Engineering a pocket synthesizer
from nothing to custom firmware on the OP-1

57 min
“I feel like a criminal and I have to be god at the same time”
Perceptions of hackers and hacktivists on their…

74 min
Let's stop EU copyright expansion
If you like untaxed links and unsurveilled uploads, you…
52 min
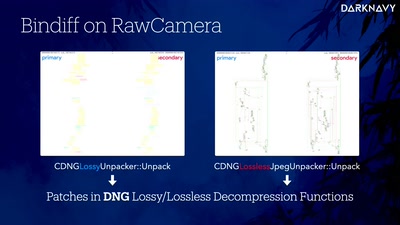
DNGerousLINK
A Deep Dive into WhatsApp 0-Click Exploits on iOS and…
59 min
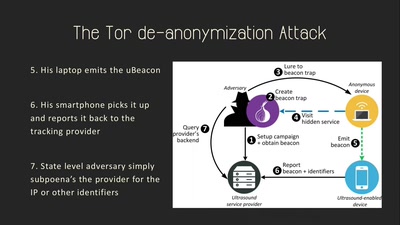
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…
59 min
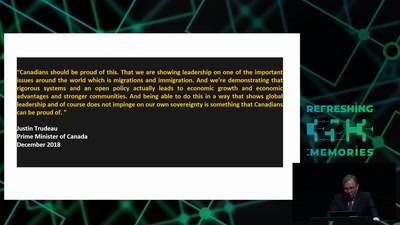
The Surveillance State limited by acts of courage and conscience
An update on the fate of the Snowden Refugees

50 min
Creating printable maps
From OpenStreetMap data to large scale maps on paper
64 min
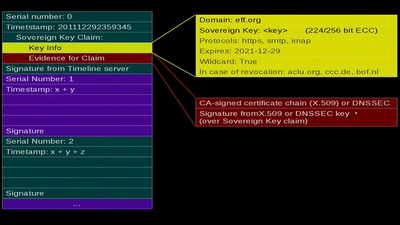
Sovereign Keys
A proposal for fixing attacks on CAs and DNSSEC
47 min
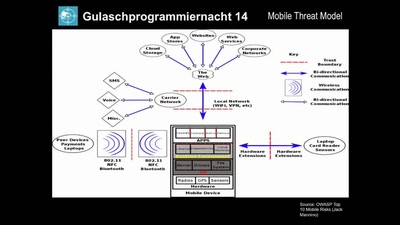
All your secrets belong to me
Why you shouldn't store secrets on a mobile device
51 min
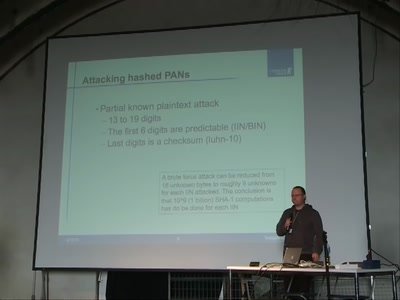
Strong encryption of credit card information
Attacks on common failures when encrypting credit card…

57 min



