Search for "ar3itrary" returned 246 results

61 min
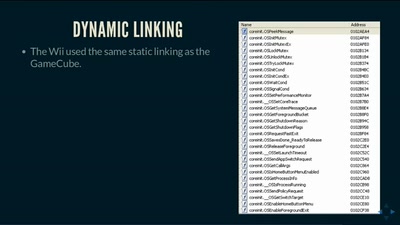
Code Pointer Integrity
... or how we battle the daemons of memory safety
36 min
Long Distance Quantum Communication
Concepts and components for intercontinal communication…

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice
42 min
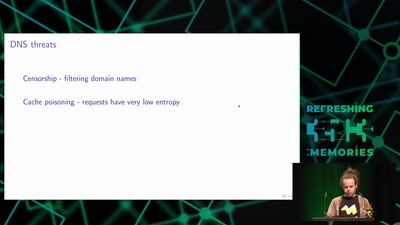
Domain Name System
Hierarchical decentralized naming system used since 30 years

60 min
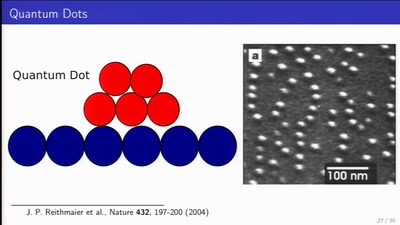
Quantum Cryptography
from key distribution to position-based cryptography
47 min
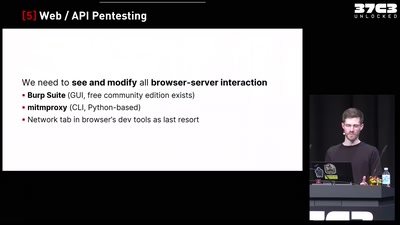
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

61 min
Safe and Secure Drivers in High-Level Languages
How to write PCIe drivers in Rust, go, C#, Swift, Haskell,…
39 min
Transmission Control Protocol
TCP/IP basics

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time
46 min
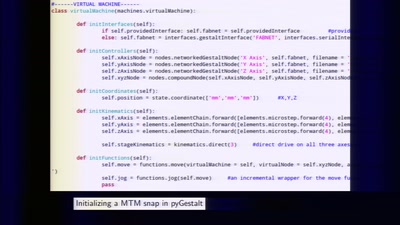
Making machines that make
rapid prototyping of digital fabrication and…

44 min