Search for "sven" returned 2148 results

26 min
Technomonopolies
How technology is used to subvert and circumvent…

41 min
Ten Years of Rowhammer:
A Retrospect (and Path to the Future)
58 min
Advanced memory forensics: The Cold Boot Attacks
Recovering keys and other secrets after power off

60 min
The Hash Disaster
Recent Results on Cryptanalysis and their Implications on…
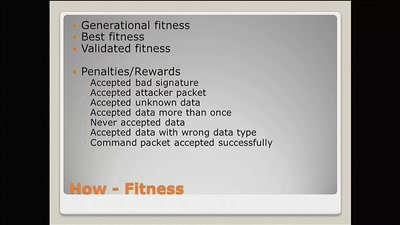
57 min
Evolving custom communication protocols
Hell Yeah, it's rocket science

30 min
Gyms, Zoos, and Museums
Your documentation should be in-game

107 min
Hacker Jeopardy
The one and only hacker quizshow

107 min