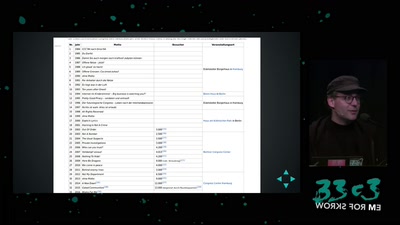
Search for "Gui" returned 1812 results
32 min
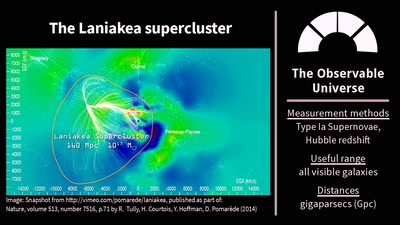
The Universe Is, Like, Seriously Huge
Stuff in Space Is Far Away – but How Do We Know?
26 min
Der 33 Jahrerückblick
Technology and Politics in Congress Talks, from 1984 to now
58 min
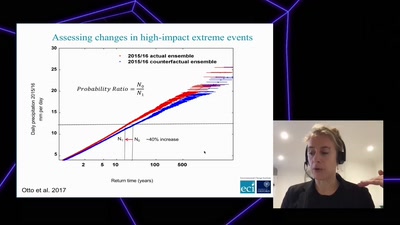
Angry weather ?
How human-induced climate change affects weather (& how we…

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics
41 min
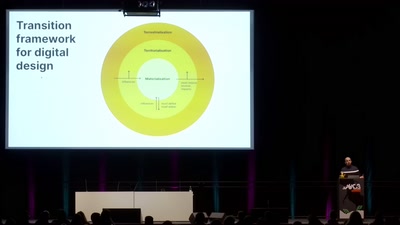
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…
29 min
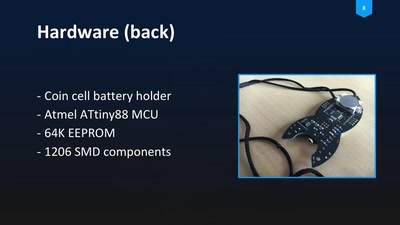
Blinkenrocket!
How to make a community project fly

60 min
Quantum Cryptography
from key distribution to position-based cryptography

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
33 min
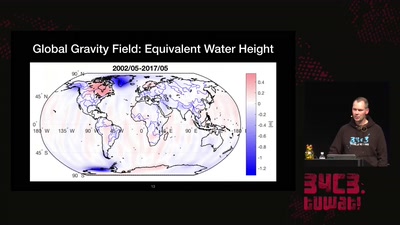
Watching the changing Earth
warning: gravity ahead
44 min
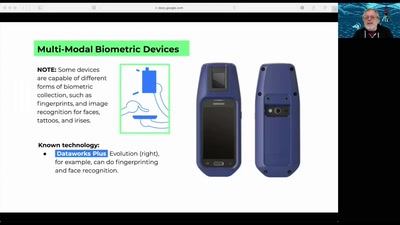
Spot the Surveillance
How to Identify Police Surveillance at Protests and Large…

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist

39 min
Tales of old: untethering iOS 11
Spoiler: Apple is bad at patching
35 min
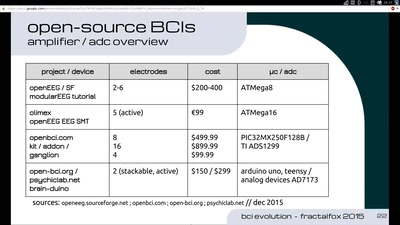
Evolution of Brain-Computer Interfaces
The future of Neuro-Headsets and concepts towards…

32 min
Visceral Systems
Approaches to working with sound and network data…

34 min
Social Cooling - big data’s unintended side effect
How the reputation economy is creating data-driven…
30 min
Automatically Subtitling the C3
How speech processing helps the CCC subtitle project, and…

30 min