Search for "jk" returned 2287 results

51 min
Wireless Drivers: Freedom considered harmful?
An OpenWrt perspective on the development of Linux 802.11…

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine

61 min
Nintendo Hacking 2016
Game Over
41 min
SCADA StrangeLove 2
We already know

60 min
Tiger, Drucker und ein Mahnmal
Neues vom Zentrum für Politische Schönheit
35 min
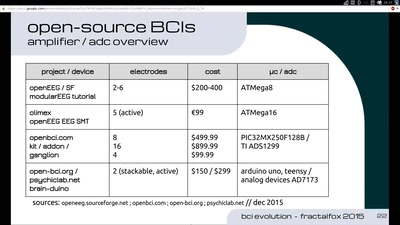
Evolution of Brain-Computer Interfaces
The future of Neuro-Headsets and concepts towards…
37 min
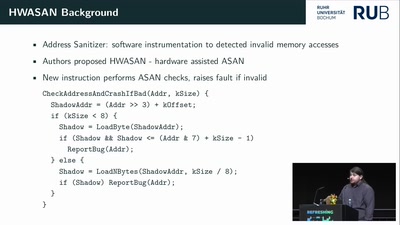
Inside the AMD Microcode ROM
(Ab)Using AMD Microcode for fun and security
47 min
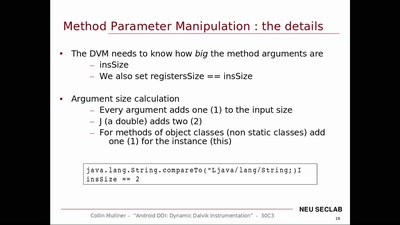
Android DDI
Dynamic Dalvik Instrumentation of Android Applications and…

60 min
Windows drivers attack surface
some 'new' insights
40 min
Never Forgetti
a didactic live-gaming performance about dying women across…

51 min
How to drift with any car
(without your mom yelling at you)

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

69 min
Telescope Making
How to make your own telescope

61 min
Uncaging Microchips
Techniques for Chip Preparation

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

59 min
Security of the IC Backside
The future of IC analysis
65 min
Rocket science – how hard can it be?
First steps into space with sounding rockets
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon

62 min