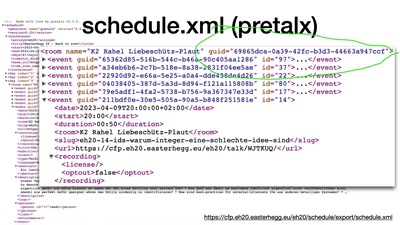
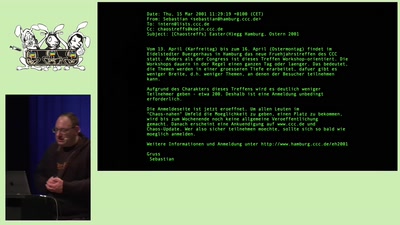
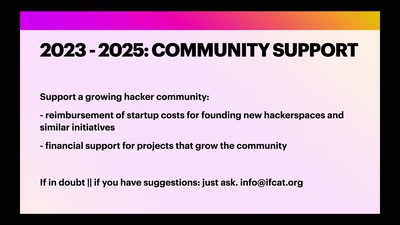
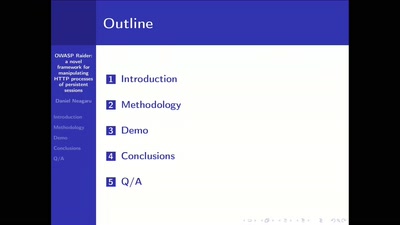
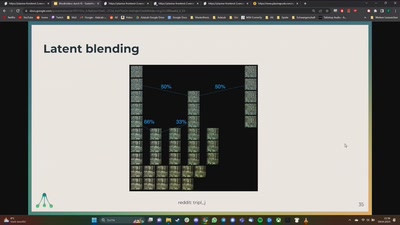
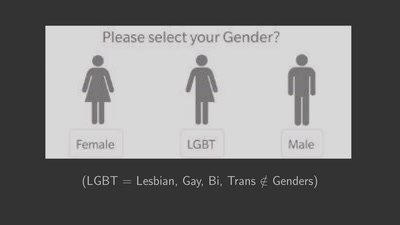
Search for "JO" returned 10053 results

60 min
Quantum Cryptography
from key distribution to position-based cryptography

60 min
30C3 Opening Event
Welcome to the 30th Chaos Communication Congress

36 min
Traut Euch, Talks zu halten
(und Artikel für die Datenschleuder zu schreiben)
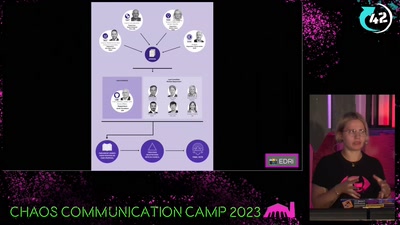
43 min
Chat-Control
now is the time to take action!

89 min
Logbuch:Netzpolitik 457
Nicht normgerecht
64 min
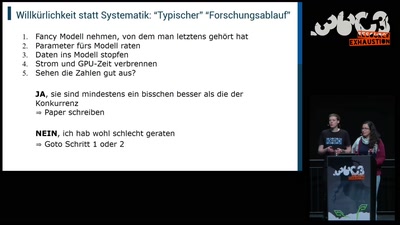
Der Deep Learning Hype
Wie lange kann es so weitergehen?

49 min
Hacking Data Retention
How bureaucrats fail to fight terror
60 min
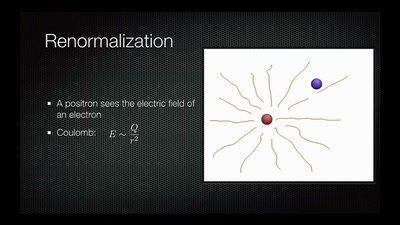
Desperately Seeking Susy
A farewell to a bold proposal?

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

55 min
Dinge, die man nicht mit Git tun sollte
Dinge, die vielleicht nicht (ganz) so optimal sind...

58 min
Energiewende & Datenschutz
Wo verlaufen die roten Linien bei der Energiewende"

33 min
Transactional Updates - deep dive
How to update your systems without breaking them

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics

53 min
Teaching machines new tricks
Machine learning: Silver bullet or route to evil?
30 min