Search for "Ari" returned 5261 results
58 min
Live Programming and Designing of Dynamic Web Applications
Towards a totally RAD development experience

65 min
There's Gold in Them Circuit Boards
Why E-Waste Recycling Is Smart and How To Make It Smarter

53 min
Blackberry: call to arms, some provided
Teach yourself upper management in 22 days
59 min
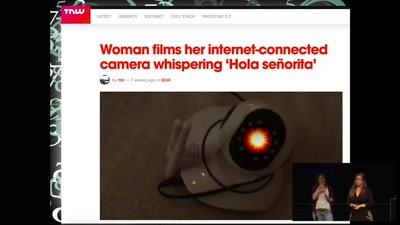
Internet of Fails
Where IoT has gone wrong

54 min
The coming war on general computation
The copyright war was just the beginning

53 min
Cryptography demystified
An introduction without maths
38 min
Rowhammer exploit
Viability of the Rowhammer Attack when ECC memory is used

49 min