Search for "Mo" returned 9989 results

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

59 min
Die Sprache der Populisten
Wie politische "Gewissheiten" sprachlich konstruiert werden
36 min
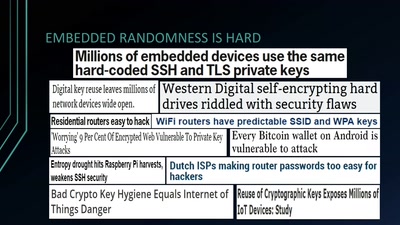
Wheel of Fortune
Analyzing Embedded OS Random Number Generators

62 min
radare demystified
after 1.0

58 min
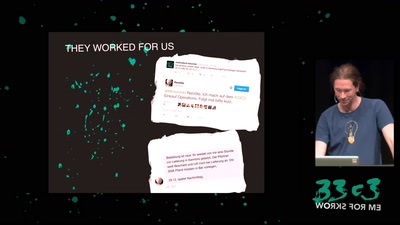
SpiegelMining – Reverse Engineering von Spiegel-Online
Wer denkt, Vorratsdatenspeicherungen und „Big Data“ sind…
62 min
Machine Dreams
Dreaming Machines
30 min
TCP Denial of Service Vulnerabilities
Accepting the Partial Disclosure Challenge

58 min
Security Failures in Smart Card Payment Systems
Tampering the Tamper-Proof

61 min
Attacking Rich Internet Applications
Not your mother's XSS bugs
38 min
NOC Review
NOC Review about the 29C3
63 min
Banking Malware 101
Overview of Current Keylogger Threats

66 min
La Quadrature du Net - Campaigning on Telecoms Package
Pan-european activism for patching a "pirated" law

59 min
SmartMeter
A technological overview of the German roll-out

49 min
Beyond Asimov - Laws for Robots
Developing rules for autonomous systems

52 min
Objects as Software: The Coming Revolution
How RepRap and physical compilers will change the world as…

27 min
Romantic Hackers
Keats, Wordsworth and Total Surveillance

61 min