Search for "Ike" returned 2798 results

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety
46 min
Maker Spaces in Favelas - Lecture
Engaging social innovation and social innovators
47 min
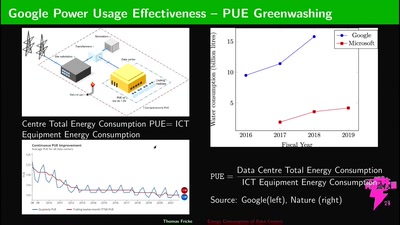
Energy Consumption of Data Centers
Problems and Solutions
61 min
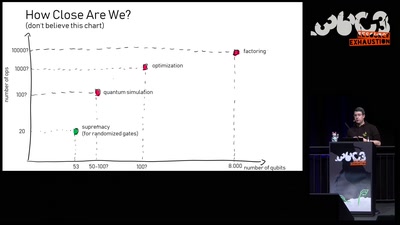
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…

120 min
Hacken, dass...?
Ack, die Wette gilt!
56 min
Making Technology Inclusive Through Papercraft and Sound
Introducing the Love to Code Platform
60 min
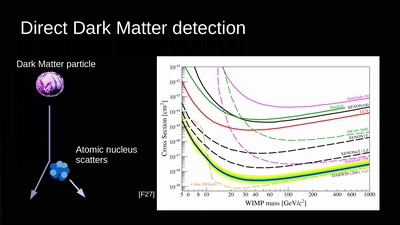
Let's reverse engineer the Universe
exploring the dark

59 min
Security of the IC Backside
The future of IC analysis

63 min
Analyze the Facebook algorithm and reclaim data sovereignty
Algorithms define your priorities. Who else besides you can…

42 min
A world without blockchain
How (inter)national money transfers works

42 min
Firmware Fat Camp
Embedded Security Using Binary Autotomy

9 min
Präsentation „Automatisierungs-Demystifizierungs-Diskurs-Maschine“
Impuls von Dr. Stefan Ullrich zur partizipativen…
115 min
Vierjahresrückblick des CCC
Nix los und viel zu tun

60 min