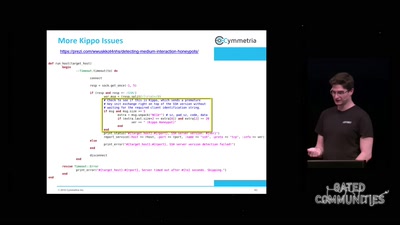
Search for "mh" returned 2881 results

45 min
To Protect And Infect
The militarization of the Internet
32 min
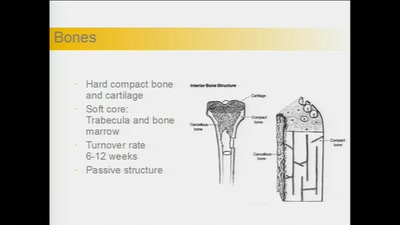
Coding your body
How to decipher the messages of your body

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

58 min
Baseband Exploitation in 2013
Hexagon challenges

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…
58 min
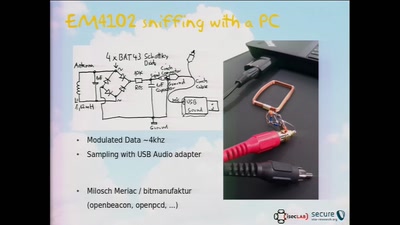
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems

38 min
The Planet Friendly Web
Warum unser Web nachhaltiger werden muss und wie wir das…

60 min
HAL - The Open-Source Hardware Analyzer
A dive into the foundations of hardware reverse engineering…

30 min
Science is broken
How much can we trust science in light failed replications,…
60 min
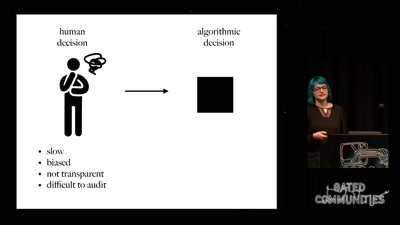
Prediction and Control
Watching Algorithms
42 min
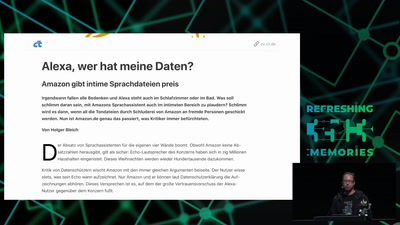
Netzpolitischer Wetterbericht 2018
Die Höhen und Tiefen der deutschen und europäischen…
43 min
unexpected coffee
a dive into industrial coffee machines

63 min
goto fail;
exploring two decades of transport layer insecurity

61 min
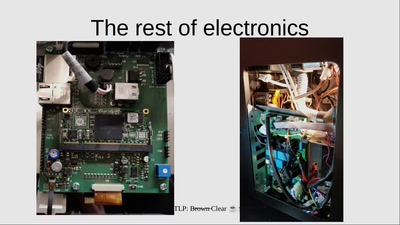
Uncaging Microchips
Techniques for Chip Preparation
42 min
Union Busting
What is it and why you should care
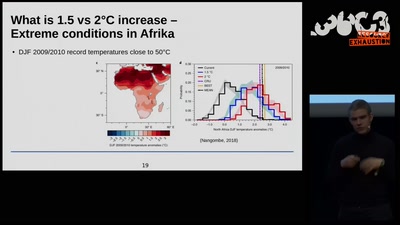
63 min