Search for "Manuel" returned 415 results
38 min
Unpacking the compromises of Aadhaar, and other digital identities inspired by it
Governments around the world are implementing digital…
47 min
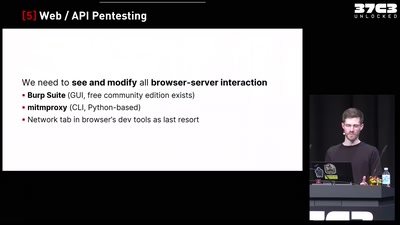
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide
55 min
YOU’VE JUST BEEN FUCKED BY PSYOPS
UFOS, MAGIC, MIND CONTROL, ELECTRONIC WARFARE, AI, AND THE…
38 min
ARMore: Pushing Love Back Into Binaries
Aarch64 binary rewriting adventures but mostly pains
60 min
Unpatchable
Living with a vulnerable implanted device
60 min
The Perl Jam 2
The Camel Strikes Back

32 min
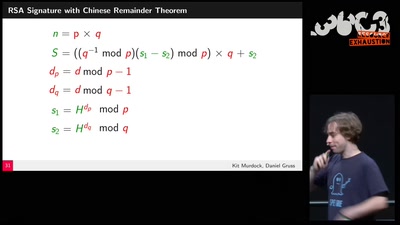
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
31 min
Nerds in the news
Spending a year coding in a newsroom

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind
38 min