Search for "_john" returned 217 results

58 min
07KINGSTON25 JAMAICA: MALARIA UPDATE Dispatches from Fort Meade
Reporting on the secret trial of Chelsea Manning

51 min
The GNU Name System
A Decentralized PKI For Social Movements

69 min
Telescope Making
How to make your own telescope

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

62 min
Transhuman Expression
Interdisciplinary research in Painting and Robotics. with…
64 min
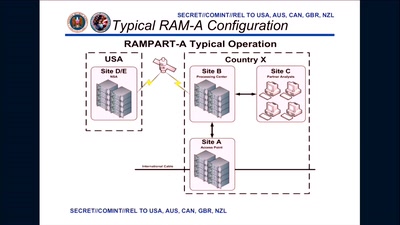
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…

62 min
Tell no-one
A century of secret deals between the NSA and the telecom…
65 min
Rocket science – how hard can it be?
First steps into space with sounding rockets

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…

120 min
Hacker Jeopardy
Zahlenraten für Geeks
128 min