Search for "Mo" returned 9996 results
57 min
Kryptographie-Hardware: Von TPMs bis Nitrokeys
– was sie versprechen, was sie können und wo sie versagen

17 min
btrfs is awesome, except when it isn't
How to fix a broken btrfs filesystem

41 min
Illumos uns gibt es noch
was läuft so im lande von Illumos
54 min
Coronary bypass at the heart of the Intertubes, badly needed
Why and how to redecentralize the Net

60 min
On working memory and mental imagery
How does the brain learn to think?
58 min
Reverse Engineering a real-world RFID payment system
Corporations enabling citizens to print digital money

74 min
Legal, illegal, decentral: Post-hacker-ethics cyberwar
Applied loss of control to hacker-ethics?

57 min
SCCP hacking, attacking the SS7 & SIGTRAN applications one step further and mapping the…
Back to the good old Blue Box?

43 min
Deploy software with systemd-sysext
Introduction to OS extensions with sysext images

60 min
ALTAIR, IMSAI, Dazzler und CP/M
Die Anfänge der individuellen Computergrafik
61 min
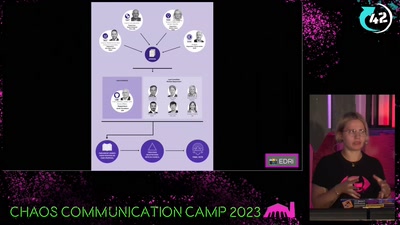
Breaking "DRM" in Polish trains
Reverse engineering a train to analyze a suspicious…
43 min
Chat-Control
now is the time to take action!

69 min
Die alternativlose Umverteilungs-Gala!
mv -r grunewald/money everyone/money
10 min
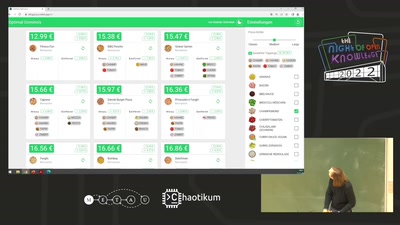
Pizza bestellen mit Dijkstra
So bestellst du die preiswerteste Pizza bei Domino’s!
64 min
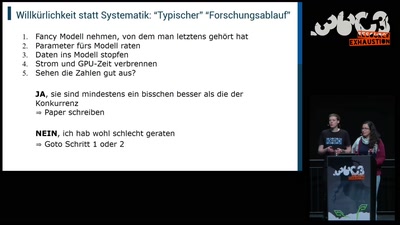
Der Deep Learning Hype
Wie lange kann es so weitergehen?

49 min
Hacking Data Retention
How bureaucrats fail to fight terror
60 min
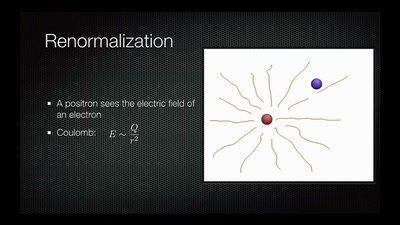
Desperately Seeking Susy
A farewell to a bold proposal?

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

89 min