Search for "Mo" returned 9996 results
49 min
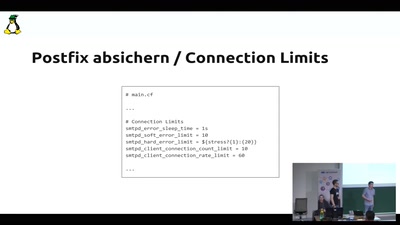
Privater Mailserver? Aber sicher!
Mit Postfix und Co zum sicheren privaten Mailserver
31 min
openPower - the current state of commercial openness in CPU development
is there no such thing as open hardware?

38 min
Schnaps Hacking
from apple to schnaps -- a complete diy-toolchain
24 min
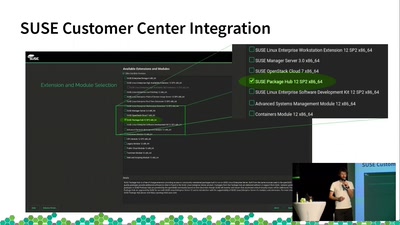
SUSE Package Hub
How to get open source packages into SLES

26 min
gcompris-qt package's journey in openSUSE
From upstream source code to Leap packaged application

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge
52 min
HowTo write a website in the Cloud
Using Amazon and Google to serve your data
42 min
Let's Encrypt
A Certificate Authority To Encrypt the Entire Web

30 min
Biometrie ist cool (nicht nur Biometrie)
wer ist Dein Gegner?

25 min
Sweetening heterogeneous Linux deployments in the Cloud with KIWI
Using KIWI to easily support multiple distributions in the…

55 min
Dinge, die man nicht mit Git tun sollte
Dinge, die vielleicht nicht (ganz) so optimal sind...

58 min
Energiewende & Datenschutz
Wo verlaufen die roten Linien bei der Energiewende"

33 min
Transactional Updates - deep dive
How to update your systems without breaking them

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics

53 min
Teaching machines new tricks
Machine learning: Silver bullet or route to evil?
30 min
Enlightenment? What is it? Why should you use it?
An Introduction to the most used Linux Desktop*

64 min
Cyberpeace and Datalove
How do we counter the memes of control?

52 min
Stuff you don't see - every day
GNU Radio Internals - how to use the Framework
47 min
Building custom initrd files
How to create a minimal bootable rescue image

29 min
Jumping the Paywall
How to freely share research without being arrested

46 min
Atmel AVR für Dummies
Was ist denn nun eigentlich so ein 'Interrupt'?

58 min