Search for "Ike" returned 2797 results

62 min
Space Ops 101
An introduction to Spacecraft Operations

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

30 min
All Our Shared Spectrum Are Belong to Us
Visualizing WLAN Channel Usage on OpenWRT

36 min
Modchips of the State
Hardware implants in the supply-chain

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…
42 min
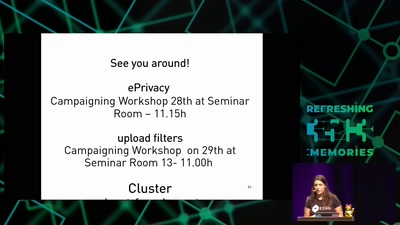
Citzens or subjects? The battle to control our bodies, speech and communications
A call to action to defend our ePrivacy and eliminate…

63 min
goto fail;
exploring two decades of transport layer insecurity

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.

54 min
What Price the Upload Filter?
The history and costs of government exceptional access

40 min