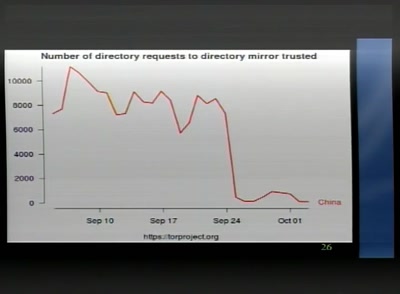
Events for tag "26c3"

126 min
Hacker Jeopardy
Number guessing for geeks

85 min
Stream: Security Nightmares
in english!!11oneeleven (translated on the fly)
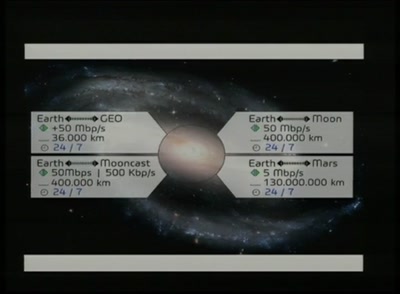
128 min
A part time scientists' perspective of getting to the moon
presenting the first German Team participating in the…
67 min
Die neokonservativen Thinktanks in der BRD
Wie SPD und CDU die gelenkte Demokratie einführen wollen
32 min
"Haste ma'n netblock?"
Layer 8 based IP Address hijacking in the end of the days…

56 min
Blackbox JTAG Reverse Engineering
Discovering what the hardware architects try to hide from…
48 min
Exciting Tales of Journalists Getting Spied on, Arrested and Deported
How their own data was taken and used against them

45 min
I, Internet
We are more Borg than we thought

49 min
The Lost Cosmonauts
Critical Thinking
37 min
Reverse-Engineering DisplayLink devices
USB to DVI for Hackers
71 min
Computer.Spiele.Politik.
Die Computerspieldebatte und wie man darin überlebt
43 min
Peanut Butter and Plastic: Industrial Revolution
Decentralized Manufacturing and Desktop Fabrication

85 min
Die Ereignisse des 12.9. und ihre Folgen
Watching them watching us: Videoüberwachung staatlichen…

59 min
Wireless power transfer
Forgotten knowledge: Tesla invented wireless power
71 min
Defending the Poor
Preventing Flash Exploits

60 min
Die Schlacht um die Vorratsdatenspeicherung
Der Stand der Debatte nach der Anhörung beim…

68 min
Weaponizing Cultural Viruses
A Manual For Engaged Memetic Resistance on The Front Lines…

53 min
Understanding Telecommunication Interception: Intelligence Support Systems
The Big Brother Services Industry and their tools

70 min
coreboot: Adding support for a system near you
Working with the open source BIOS replacement and getting a…
62 min
Cybernetic Cannibalism
Why is Brazil the country of the future?
41 min
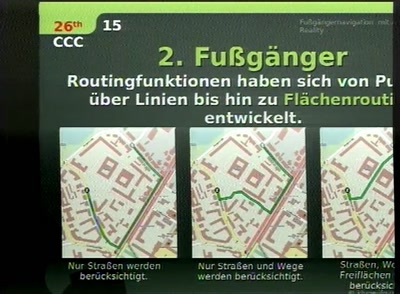
Fußgängernavigation mit Augmented Reality
Navit - Navigationssystem

64 min
Europäische Biometriestrategien
Die Automatisierung von Personenidentifizierung an der…

41 min
Homewreckery
Electrifying the Thread out of Clothing

63 min
WikiLeaks Release 1.0
Insight into vision, motivation and innovation
78 min
Fnord-Jahresrückblick 2009
Von Abwrackprämie bis Zensursula
79 min
Stream: Fnord-Jahresrückblick 2009
German / English version of the Fnord-Jahresrückblick 2009.

140 min
Lightning Talks - Day 4
4 minutes of fame

73 min
Conlanging 101
I make languages (and you can too)
65 min
Why Germany Succeeded Where America Has Failed in Achieving Meaningful Voting Computer…
And Why All Democracies Should Follow

63 min
Die Verwaltung rüstet auf - der digitale Steuerbürger
Gefahren, Nutzen, Risiken für Jedermann

64 min
A Hacker’s Utopia
What's There and What's Missing
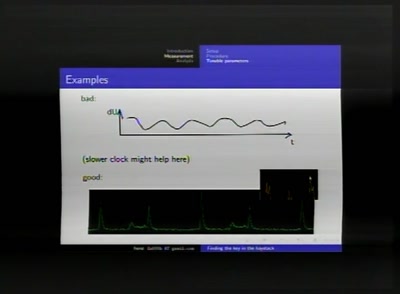
50 min
Finding the key in the haystack
A practical guide to Differential Power Analysis

40 min
Wolpertinger. Ein verteilter Portscanner.
Schneller scannen!

102 min
Nougatbytes - Ein Wortspiel, bunt und in stereo
Die geekige Bilderrätselspielschau
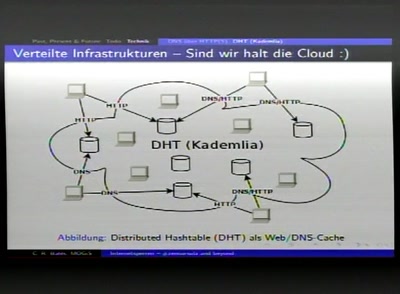
46 min
Internetsperren
#zensursula and beyond

57 min
SCCP hacking, attacking the SS7 & SIGTRAN applications one step further and mapping the…
Back to the good old Blue Box?
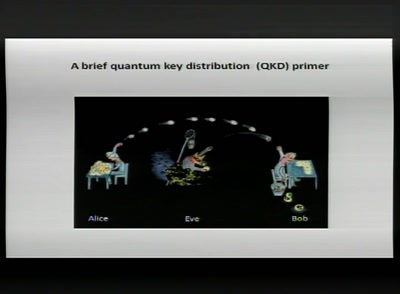
52 min
How you can build an eavesdropper for a quantum cryptosystem
hardware demo during the lecture
61 min
Hacking the universe
When strings are super and not made of characters
59 min
Here Be Electric Dragons
Preparing for the Emancipation of Machines

61 min
DECT (part II)
What has changed in DECT security after one year

136 min
Lightning Talks - Day 3
4 minutes of fame

54 min
Eine Zensur findet statt
Eine Rundreise durch die Welt der Zensur – Wo, Was und Wie?

57 min
Why Net Neutrality Matters?
Status update on current legislation, campaigns and actions

118 min
Lightning Talks - Day 1
4 minutes of fame
58 min
Privacy & Stylometry
Practical Attacks Against Authorship Recognition Techniques
60 min
After the Hype
The current state of One Laptop per Child and Sugar Labs
59 min
Location tracking does scale up
How skyhook wireless tracks you continously

63 min
Liquid Democracy
Direkter Parlamentarismus – gemeinsam verbindlich…
49 min
Here be dragons
Keynote

62 min
ETSI-Vorratsdatenspeicherung 2009
und andere Sockenpuppen der GCHQ
52 min
Im Herz der Bestie
Medien hacken

55 min
Wofür offenes Internet?
Warum wir klare Regeln für Netzneutralität brauchen
132 min
Lightning Talks - Day 2
4 minutes of fame
59 min
Vom Kreationismus zum Kollektivismus
Fehlende Einsicht in die Leistung komplexer Systeme

52 min
our darknet and its bright spots
building connections for spaces and people
47 min
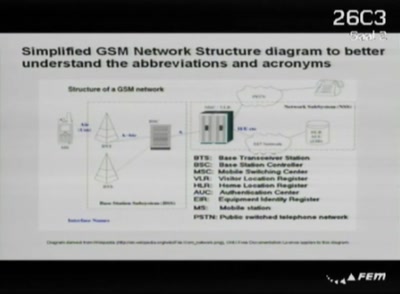
Playing with the GSM RF Interface
Doing tricks with a mobile phone
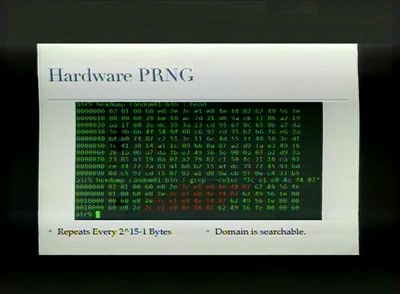
55 min
Building a Debugger
Open JTAG with Voltage Glitching
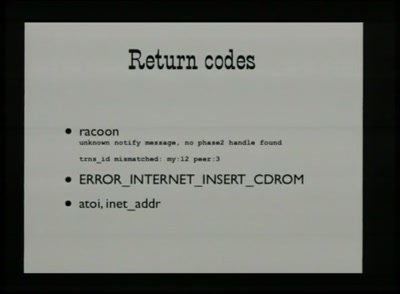
54 min
Vier Fäuste für ein Halleluja
Geschichten aus dem API-und Protokollkrieg von zwei…

51 min
Advanced microcontroller programming
Getting deeper into AVR programming

60 min