Search for person "Ralf Mueller von der Haegen" returned 145 results

47 min
Olmogo - because it's your data!
A cryptographically secure social network platform

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques

136 min
CyberMorning Show
Cyber Gulasch

60 min
Flip Feng Shui
Advanced Rowhammer exploitation on cloud, desktop, and…
54 min
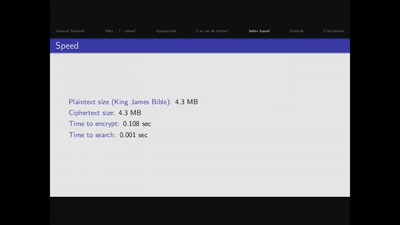
The World of Searchable Encryption
A glimpse into advanced cryptogrpahic schemes
45 min
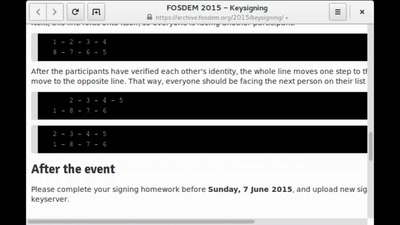
Two decades later - Keysigning in the 2000s
Micro keysigning parties for the masses

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

58 min
PLC-Blaster
Ein Computerwurm für PLCs
70 min
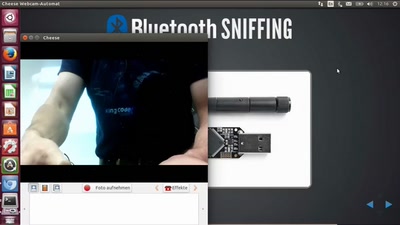
Attacking IoT Telemetry
A study of weaknesses in the pipeline of rapidly advancing…

73 min
What's cooking in GNOME?
GNOME 3.12 - Design Decisions, Main Changes, Future Visions
49 min