Search for person "Roland van Rijswijk-Deij" returned 157 results
63 min
LightKultur in Deutschland
Clubkultur oder wie modern ist unser Kulturbegriff?
65 min
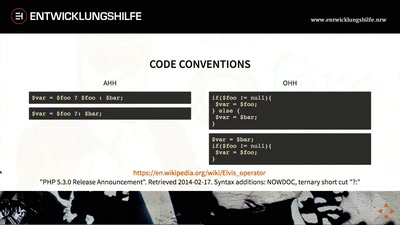
Clean Code
Benefits Code Refactoring

25 min
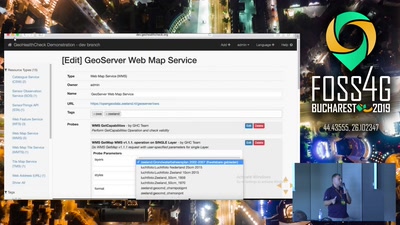
GeoHealthCheck
Uptime and QoS monitor for geospatial web-services
58 min
Are all BSDs created equally?
A survey of BSD kernel vulnerabilities.

44 min