Search for person "Walter van Holst (Vrijschrift)" returned 141 results
58 min
Are all BSDs created equally?
A survey of BSD kernel vulnerabilities.

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene

44 min
Life Needs Internet
Documenting digital culture through handwritten letters

31 min
PUFs, protection, privacy, PRNGs
an overview of physically unclonable functions

42 min
A world without blockchain
How (inter)national money transfers works

53 min
Smart, safe & happy
ensuring civil rights in the digital era

27 min
Detecting a breach from an attackers perspective.
We're gonna regret this
58 min
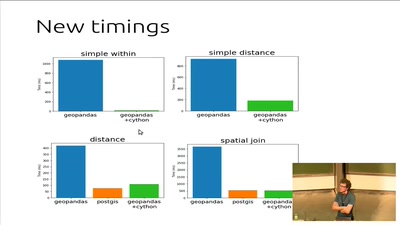
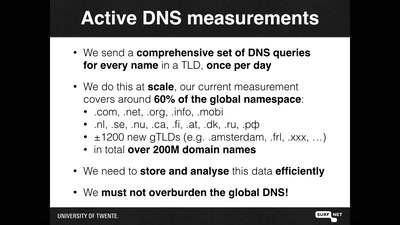
OpenINTEL: digging in the DNS with an industrial size digger
I measured 60% of the DNS, and I found this

60 min
Flip Feng Shui
Advanced Rowhammer exploitation on cloud, desktop, and…

53 min
TBM: Trusted boot module
NLNet sponsored (open hardware) trusted boot module

60 min
Windows drivers attack surface
some 'new' insights
82 min
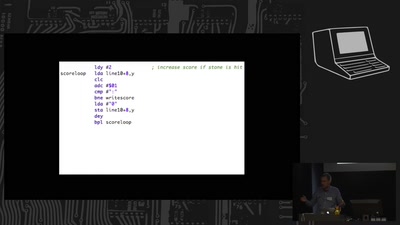
Maker-Board meets Chiptunes
8-Bit-Rechner als Musikinstrumente

45 min