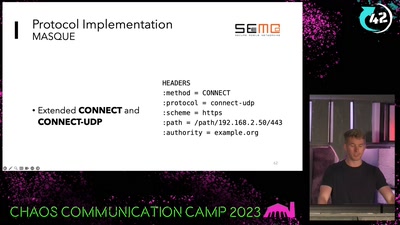
Search for "Max" returned 4566 results

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…
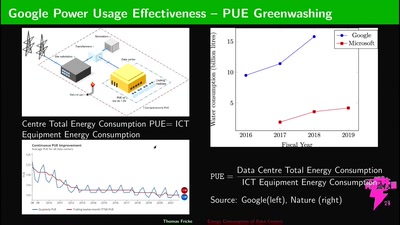
47 min
Energy Consumption of Data Centers
Problems and Solutions

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…

42 min
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

37 min
The foodsaving grassroots movement
How cooperative online structures can facilitate…

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

35 min
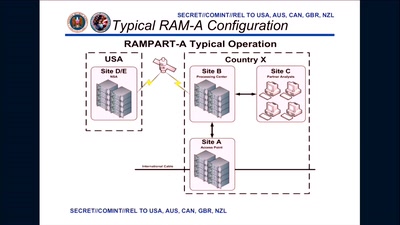
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution
64 min
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…
28 min
Vision Weiße Ware
Von der unreparierbaren Black-Box zur transparenten…

32 min
Verified Firewall Ruleset Verification
Math, Functional Programming, Theorem Proving, and an…

32 min
Think big or care for yourself
On the obstacles to think of emergent technologies in the…
43 min