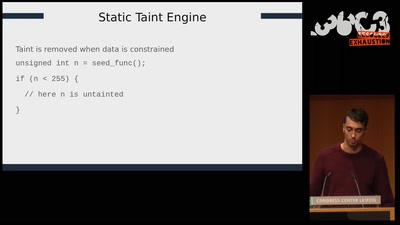
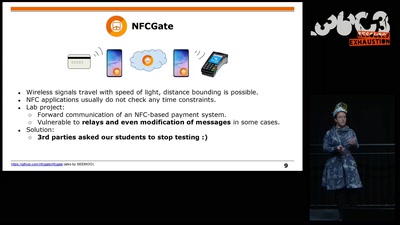
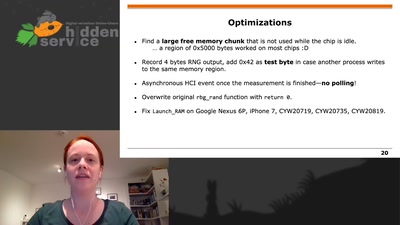
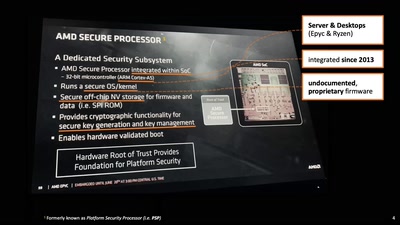
Search for "sECuRE" returned 792 results

63 min
All cops are broadcasting
TETRA unlocked after decades in the shadows

62 min
Let's Encrypt
A Free Robotic Certificate Authority

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

58 min
Uncertain Concern
How Undocumented Immigrants in the US Navigate Technology

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

36 min
Modchips of the State
Hardware implants in the supply-chain

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption
38 min