Search for "Huy" returned 1354 results

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)

29 min
The Urban Organism
Hacking [in] Hong Kong
38 min
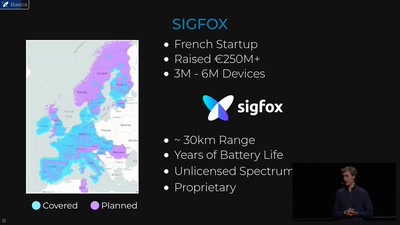
Hunting the Sigfox: Wireless IoT Network Security
Dissecting the radio protocol of Sigfox, the global…

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

32 min
What's It Doing Now?
The Role of Automation Dependency in Aviation Accidents

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people
33 min
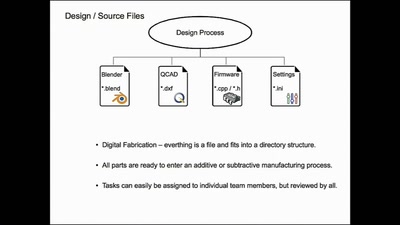
Structuring open hardware projects
experiences from the “i3 Berlin” 3D printer project with…

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…
62 min
Machine Dreams
Dreaming Machines
33 min
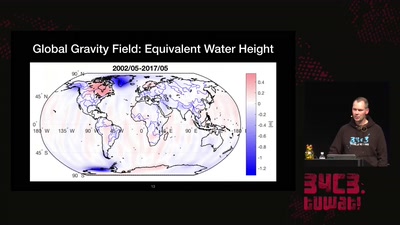
Watching the changing Earth
warning: gravity ahead

46 min
Writing secure software
using my blog as example

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

63 min
Synthetic Sentience
Can Artificial Intelligence become conscious?

55 min
The DROWN Attack
Breaking TLS using SSLv2
47 min
Jailbreaking iOS
From past to present

45 min