Search for "Bea" returned 6111 results

55 min
The DROWN Attack
Breaking TLS using SSLv2

32 min
Verified Firewall Ruleset Verification
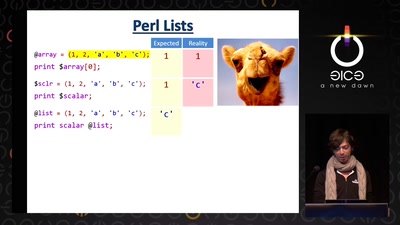
Math, Functional Programming, Theorem Proving, and an…
40 min
Art against Facebook
Graffiti in the ruins of the feed and the…

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…

44 min
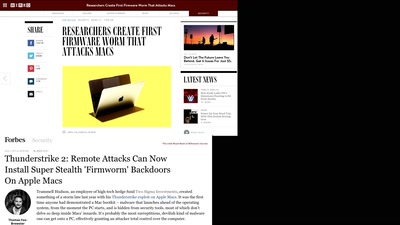
Exploiting PHP7 unserialize
teaching a new dog old tricks

29 min
The Pirate Cinema
Creating mash-up movies by hidden activity and geography of…

53 min
When algorithms fail in our personal lives
Social media break up coordinator
33 min
Structuring open hardware projects
experiences from the “i3 Berlin” 3D printer project with…
30 min
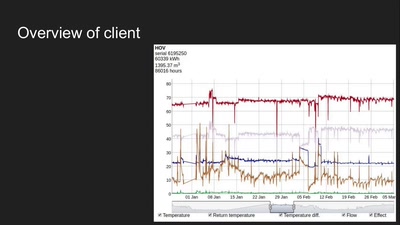
“Nabovarme” opensource heating infrastructure in Christiania
Freetown Christiania´s digitally controlled/surveyed…

61 min
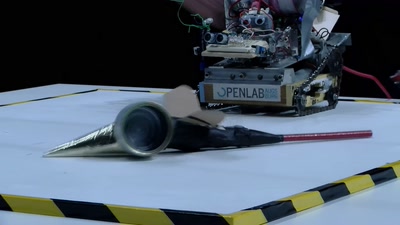
Nintendo Hacking 2016
Game Over
60 min
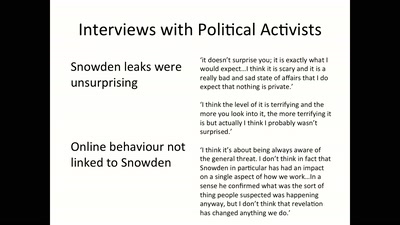
Media Coverage and the Public in the Surveillance Society
Findings from a Research Project on Digital Surveillance…

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems
20 min
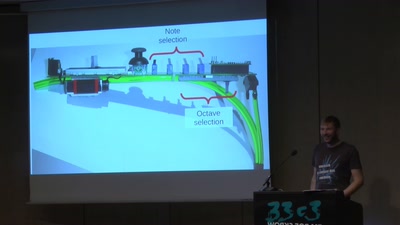
The Nibbletronic
A DIY MIDI Controller and a New UI for Wind Instruments

54 min