Search for "John" returned 1055 results

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

63 min
Reconstructing narratives
transparency in the service of justice
40 min
Welcome Pattern - Theorie und Praxis
(Eine Gemeinschaftsproduktion der Haecksen, der…

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level
60 min
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…

32 min
Fuck Dutch mass-surveillance: let's have a referendum!
Forcing the Netherlands to publicly debate privacy and the…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

58 min
Switches Get Stitches
Industrial System Ownership
61 min
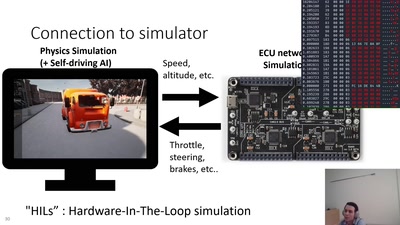
RAMN: Resistant Automotive Miniature Network
A safe platform to study and research automotive systems
59 min
Let's build a quantum computer!
Understanding the architecture of a quantum processor
59 min
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent
46 min
Maker Spaces in Favelas - Lecture
Engaging social innovation and social innovators
56 min
Running your own 3G/3.5G network
OpenBSC reloaded

60 min
What does Big Brother see, while he is watching?
Uncovering images from the secret Stasi archives.
60 min
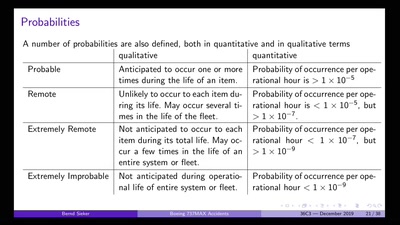
Boeing 737MAX: Automated Crashes
Underestimating the dangers of designing a protection system
63 min
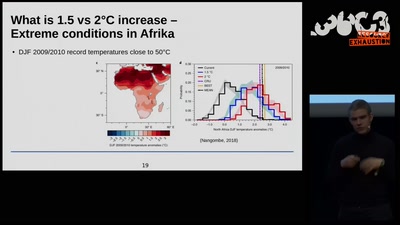
Science for future?
What we can and need to change to keep climate change low -…

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…
39 min