Search for "Mitch" returned 1255 results

30 min
Syrian Archive
Preserving documentation of human rights violations

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it
43 min
#xfilesgdpr
Datenschutz-Mythen aus 5 Jahren DS-GVO
42 min
Netzpolitischer Wetterbericht 2018
Die Höhen und Tiefen der deutschen und europäischen…

38 min
Afroroutes: Africa Elsewhere
VR experience "Beyond Slavery"

40 min
Das Mauern muss weg
Best of Informationsfreiheit
39 min
The Eye on the Nile
Egypt's Civil Society Under Attack
31 min
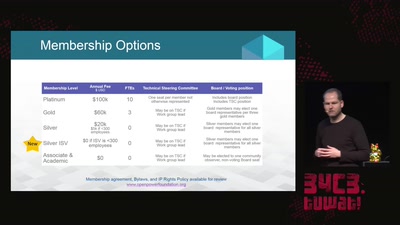
openPower - the current state of commercial openness in CPU development
is there no such thing as open hardware?
59 min
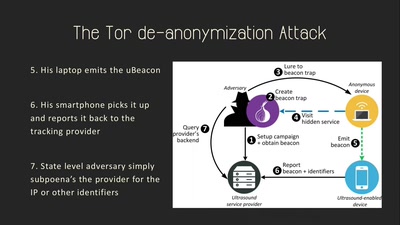
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…
58 min
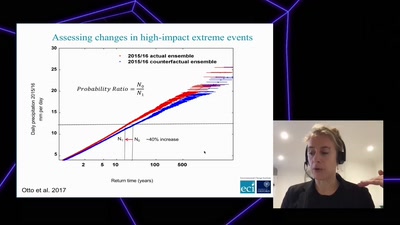
Angry weather ?
How human-induced climate change affects weather (& how we…

24 min
The Four Wars
Terror, whistleblowers, drugs, internet

48 min
Seidenstraße
The Making of…
32 min